Short version: Telus installed an upgraded network device. First it broke our landline phone, then our inbound network connectivity thereby disconnecting my blogs. I spent hours on the phone with Telus support, and fixed one of those problems myself despite their ‘help’. The phone still didn’t work, then a really good Telus technician came and solved all the problems..
Longer version… continue reading.
The undesired upgrade
We pay quite a lot to Telus for our various home services. In total our fees come to about $250 – $300 a month for internet, TV, and landline phone- this total excludes what we pay for cellular. The figure noted is when we are getting ‘discounts’ which expire every two years.
The two year contract expiry always seems to come as a surprise to me, noticed primarily by the increase in monthly fees of about $100. I then call Telus service and we ‘negotiate’ a contract update that usually involves changes in our services. Generally I don’t particularly want these changes: I just want the reduced prices that come along with them.
Two years ago when I did this dance with Telus we ended up with a home ‘security’ camera that I don’t want. This time we ended up with an upgrade from 1 Gbps to 1.5 Gbps Purefibre internet services. I don’t mind the extra bandwidth, but apparently this change requires replacing the on-premises Telus equipment- specifically installation of a new ‘network access hub’ (NAH).


The new NAH supports up to 10 Gbps, which is nice and makes me think it might last a few years. The installer came and did their magic and everything worked as it had before except for our landline phone. The technician indicated he would put in a work order for the phone services to be updated and it should be fixed within a few hours.
The broken landline phone service
The next day our landline phone was still not working so I first tried calling the technician’s number. After I got no answer there I called Telus support. This began a call that lasted over two hours during which I both rebooted and did a factory reset (more on that later) of the NAH. None of this actually got the phone working.
The Telus support person said they would have to dispatch a technician to our home to figure out the problem. This person would not be able to come ‘for several days’, so we resigned ourselves to being without a landline for a while longer.
After I got off the phone with Telus I was puttering and noticed that I could no longer access my blogs: something that had been done during the call with Telus support had ‘broken’ inbound connectivity to my home services.
Getting the inbound / blog connections working
My blog network config
My blogs are important to me despite being ‘non-critical’ to the world in general, so I called Telus support back and started a new discussion. As always I struggled to get the support person to understand both the problem and my observations about it.
My blogs run on a small server which attaches to a firewall appliance that runs PFSense: that same firewall protects the rest of our LAN. Everything was working prior to the activities related to trying to get the landline services operational. Also prior to those activities, the firewall had been assigned a publicly accessible IP address by the NAH- that address had been in the 207.x.x.x range.
- My blog also uses Cloudflare as a DoS filter and CDN, but that is something that really confuses the Telus support people so I tried to not focus on that
My hypothesis for cause of the failure
Access to my blogs broke after the Telus-support guided attempts to get the phone services working. This implied to me that something we had done had disrupted inbound access on the HTTP ports (port 80 and 443) used by the blogs. I observed that:
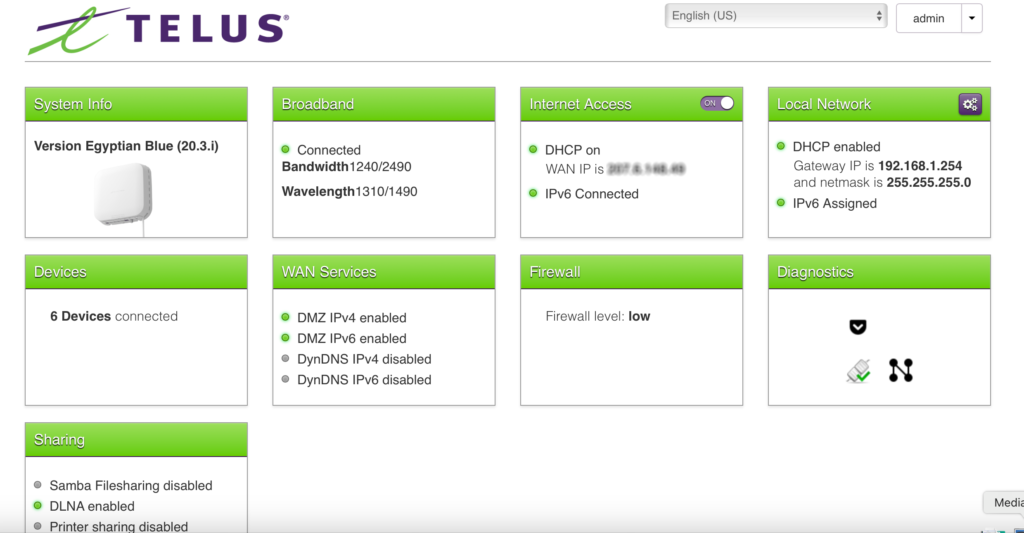
- my firewall was now being issued a non-routable IP address in the 192.x.x.x range
- I could see that my firewall was correctly detecting the public address that was being NATted (which was in the 108.x.x.x range) and had properly updated itself and Cloudflare with this detail
- I couldn’t connect to my blog even by using the public address directly
- I could confirm that my blog was working by connecting to it on my LAN; this isn’t easy as it requires using a browser that allows using ‘invalid’ certificates as my site exclusively uses HTTPS
All of these factors led me to hypothesize that the NAH had originally been configured differently e.g.: without a NAT configuration or with some kind of port forwarding/DMZ configured for my internal network. Further, I guessed that these settings had been ‘undone’ by the factory reset I had been asked to perform earlier. Unfortunately, I couldn’t tell the Telus support folks exactly what to fix because I didn’t know the NAH device in question or what its configuration settings were.
Fixing it myself… kinda
Trying to explain this to the Telus support guys on the phone was incredibly frustrating. Towards the end after over two hours on the line (and nearing five hours for the day) I was getting rather curt with the poor support tech. I am sorry to admit that I started doing the “I worked in IT for 40 years, so please listen to what I’m saying” thing.
During one of the interminable sessions of being on hold I started doing some googling on interacting with the Telus NAH. I learned how to connect to its admin UI and where to find the device admin ID and password.
- NAH address: 192.168.1.254 (but also found under the front cover)
- NAH password: ( look under the front cover )
- how to take off the front cover=> https://imgur.com/a/G5fw8Vc
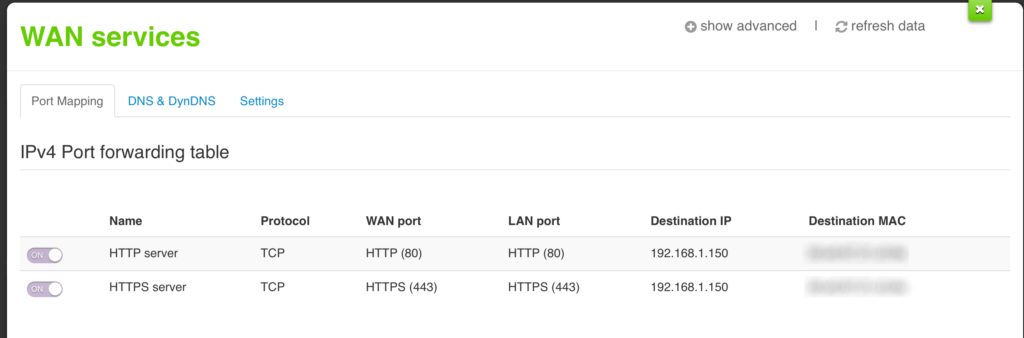
Using this UI I was able to find settings that got me to a ‘working’ configuration for inbound network traffic to my blogs. First I tried enabling a DMZ configuration under the “WAN Services” heading. This seemed to work for a while, but then it stopped- I’m not sure why.
So I disabled the DMZ settings and tried again, this time using port forwarding (WAN Services=> Port forwarding; turn on “Advanced” to add new ports to forward). I added forwarding rules for port 80 and 443 to the IP address assigned to the firewall; this ends up looking something like this:
This got things working just as the Telus support guy returned from hold to tell me to try connecting to the NAH and making changes to the DMZ settings. Amazing… but we weren’t done yet.
And then came Sean…
The landline phone still wasn’t working. And to be honest I wasn’t really ‘happy’ with the use of port forwarding on the NAH. In this configuration the NAH was forwarding ports to my firewall which then forwards them to my blog, which seems unnecessarily complicated. I had come across settings in the NAH configuration UI for bridging and for disabling NAT services, and was suspicious that the NAH could be told to get out of the way of my firewall entirely. But I didn’t even want to try explaining that to the Telus support guys I had been talking to.
Telus had me scheduled for a technician visit sometime next week, so… maybe that guy could help?
I received a call on my cell (remember- landline was still broken at this point) early on Friday from a Telus technician named “Sean”. He offered to come by immediately to fix the landline phone services as his schedule had cleared up, and I said “Sure, but can you also look at these other issues with the NAH?” Amazingly, Sean seemed to understand exactly what I was saying about my firewall, port forwarding, public (routable) versus non-routable IP addresses… I became cautiously optimistic.
My caution was unfounded. Sean was a joy to work with: he got our phone working in under 15 minutes, then set about revising the NAH configuration. He enabled bridging (later had to revise this to ’10G bridge’ to only activate bridge mode on a single port so the Optik DVR wasn’t also issued with public IPs) and boom: my firewall was getting a publicly routable IP address. All of this was done while we chatted about UPSes, rack mounted computing/network devices, cellular service, and the joys of living in a rural area.
All it takes is one good person to turn around two days of frustration, fuss, and bother. I’ve often found that Telus home-visit technicians are great to work with: Sean is top of that lofty heap. I just wish their phone support services were up to this same standard. Regardless: I’m back to being a Telus internet fan after a few days of trials and tribulations almost turned me against them.
The ‘ultimate’ configuration
Final settings via the NAH UI:
- Plug my internal firewall into the 10G (10 Gbps) port, and the Telus Wifi hub into one of the other (2.5 Gbps) ports

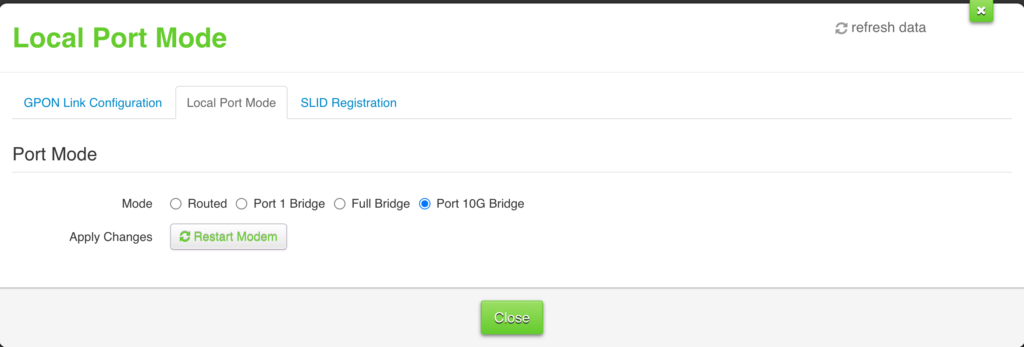
- In the NAH admin UI under “Broadband”, select the “Local Port Mode” tab…
- Choose “Port 10G Bridge”…
- note: choosing “Routed” puts the NAH back into its default mode; choosing “Full bridge” or “Port 1 bridge” seems to give all the ports public IPs, which is not desirable for security of the Telus Optik device etc.
- also note that Telus ‘allocates’ two (2) public IPs per Purefibre client, so making all the ports public is likely to result in problems down the road
- note: choosing “Routed” puts the NAH back into its default mode; choosing “Full bridge” or “Port 1 bridge” seems to give all the ports public IPs, which is not desirable for security of the Telus Optik device etc.
- Click the “Restart Modem” button: the NAH UI should say ‘please wait’ or something similar while it reboots
Note that the NAH UI will be ‘inaccessible’ from the firewalled LAN in this configuration. To access the NAH web UI you’ll have to connect to the Telus Wifi device.